PostgreSQL - Password complexity, enabling passwordcheck

Hello colleagues.
In today's article, we'll show you how to set PostgreSQL password complexity checking mechanism when creating a new user or role in a database, or when changing an existing user or role.
The passwordcheck plugin is responsible for checking password complexity in PostgreSQL. The plugin will check the password whenever a new database role or user is created, or when the password of an existing role or user is changed.
First of all, you need to check whether you have the passwordcheck plugin enabled in PostgreSQL or not, for this we execute a simple query in the database console:
sql> SHOW shared_preload_libraries;
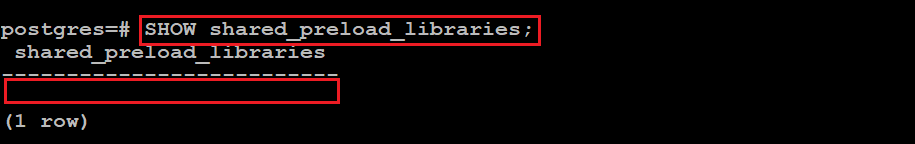
In our case, we returned an empty value, which means that the passwordcheck plugin is disabled for us.
To enable the plugin, you need to find the shared_preload_libraries parameter in the main configuration file postgresql.conf and add the $libdir/passwordcheck values to it.
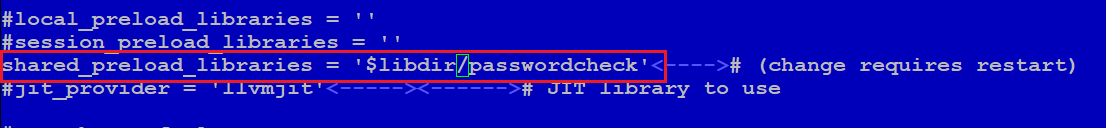
After adding the parameter, be sure to restart the database, otherwise the plugin will not be active.
If, after restarting the database, we get an error at startup, and the DBMS shows an error with an example text that it does not know such a plugin and cannot connect it, then when you compiled your DBMS, you did not specify which extensions you want to install together with DBMS.
You need to build your DBMS before using the configure utility that comes with the DBMS.
If everything worked out for you and your database started successfully after adding the parameter, now let's check the states of the shared_preload_libraries variable in the console again.
sql> SHOW shared_preload_libraries;
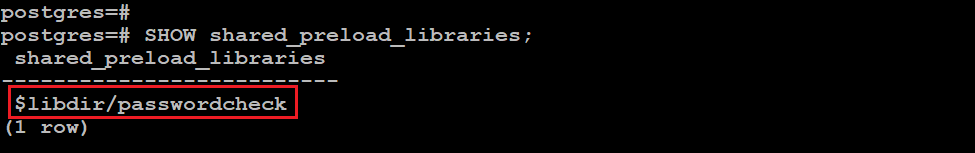
As you can see, as a result, the plugin was successfully activated.
Now it's the turn to check how the plugin will work if we try to create a role with too simple passwords.
sql> CREATE ROLE test WITH LOGIN PASSWORD '123';
sql> CREATE ROLE test WITH LOGIN PASSWORD 'test';
sql> CREATE ROLE test WITH LOGIN PASSWORD 'postgres';
sql> CREATE ROLE test WITH LOGIN PASSWORD 'postgresql';
sql> CREATE ROLE test WITH LOGIN PASSWORD 'postgresqlqqqkjhkh';
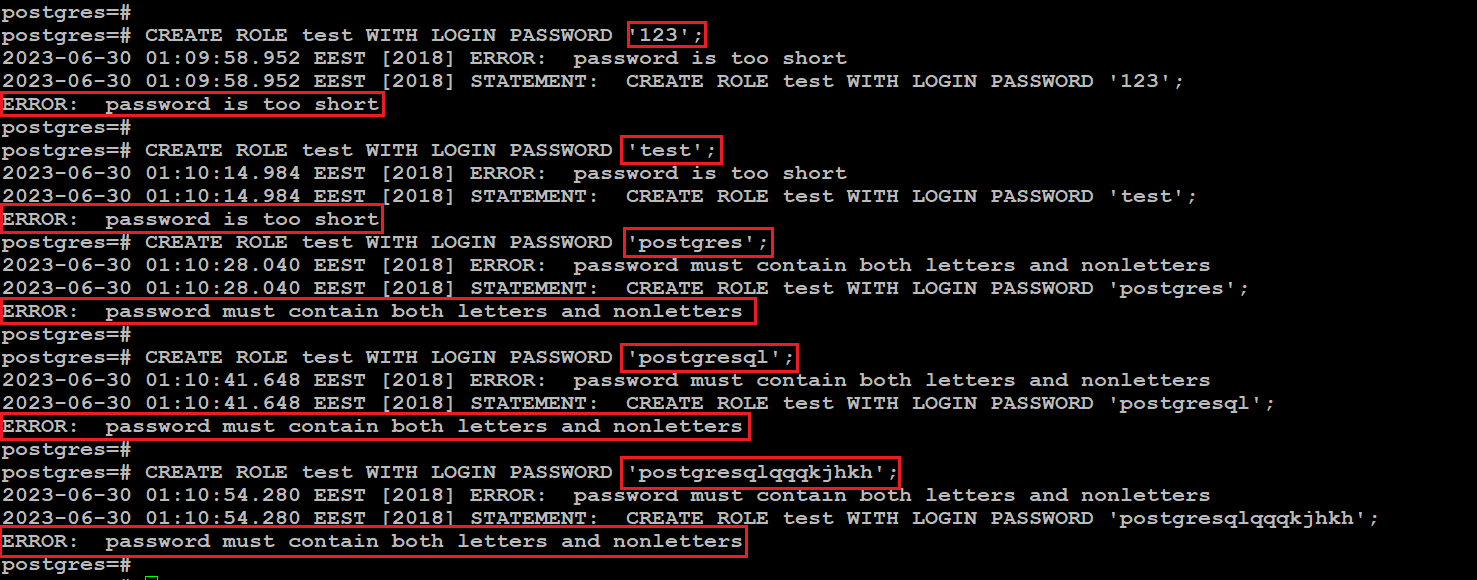
As you can see, the plugin successfully fights so that we cannot create a role with a weak password.
Thank you all, I hope my article was of some help to you.


